
On October 21, 2024, the U.S. Department of Justice (DOJ) issued a Notice of Proposed Rulemaking (NPRM)1 to implement Executive Order 14117,2 which authorizes the Attorney General to prohibit or restrict transactions by U.S. persons that could result in the transfer of government-affiliated or bulk U.S. sensitive data to countries of concern or covered persons, and to provide safeguards around other activities that may otherwise provide access to such data. The NPRM provides an opportunity for members of the public to provide comments by November 29, 2024. The proposed rules also build upon the Advance Notice of Proposed Rulemaking (ANPRM) issued by the DOJ in February 2024, which we analyzed in a prior Client Alert.
Key Takeaways
- The proposed rules mark the emergence of the DOJ’s National Security Division as an important future regulator of the flow of data across borders. This development and the concerns underlying the proposed rule reflect a deepening set of national security concerns regarding access to U.S. sensitive data by China and other countries of concern. Those concerns will continue to intersect with growing data privacy concerns regarding access to U.S. personal data and growing restrictions on the sharing of other forms of sensitive data with parties in China, such as controls on the export of various kinds of software and technology, as previewed in our prior Client Alert.
- While several commenters at the ANPRM stage requested that the DOJ create exceptions for encrypted, pseudonymized, de-identified, or aggregated data, the DOJ ultimately declined to do so in the NPRM, citing the new regime’s focus on national security vs. privacy. Similarly, the DOJ notes that the consent of the subject to share sensitive data will also not be written in as an exception, despite commenter requests. As a result, the new rules will prove a more rigid bar to certain types of data transfers and may capture unexpected commercial transactions. For example, many transactions that parties may not otherwise think of as transfers of personal data—e.g., transfers of biological material associated with anonymous subjects—may end up covered by the new rules.
- The proposed rules also introduce new hurdles for companies engaged in certain data transactions involving bulk U.S. sensitive personal data with countries of concern or covered persons. U.S. sensitive personal data encompasses precise geolocation data and covered personal identifiers, which are commonly held sensitive personal data types of technology companies, as well as human genomic data and other kinds of health-related information. Some such transactions would be prohibited altogether, which may force significant changes to existing business models in industries ranging from pharmaceuticals to adtech. In many other cases, companies seeking to engage in such data transactions would face a range of new privacy compliance requirements under the proposed rule, such as the security requirements developed by the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Agency (CISA), as well as new recordkeeping and audit obligations. Alternatively, companies would need to seek a general or specific license from the DOJ.
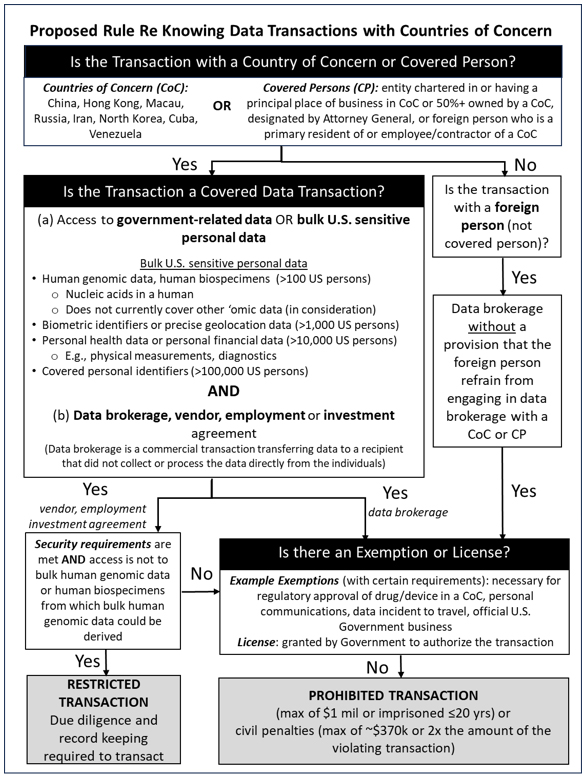
I. Transaction Parties: U.S. Persons, Countries of Concern, and Covered Persons3
Under the NPRM, the set of U.S. persons restricted will include any U.S. citizen, national, refugee, asylee, or lawful permanent resident; any entity organized under U.S. law, including foreign branches thereof; and any person resident in the United States. In addition, as discussed below, in certain circumstances foreign parties may end up complying with the rules by virtue of the restrictions placed on their U.S. citizen employees or other decision-makers.
Meanwhile, the designated countries of concern are the People’s Republic of China (PRC, which for purposes of the NPRM includes Hong Kong and Macau), Russia, Iran, North Korea, Cuba, and Venezuela. A covered person is a foreign person primarily residing in a country of concern, or: 1) is 50 percent or more owned, directly or indirectly, by a country of concern; 2) is organized or chartered under the laws of a country of concern; 3) has its principal place of business in a country of concern; 4) is 50 percent or more owned, directly or indirectly, by a covered person; 5) is an employee or contractor of a covered person; or 6) is designated by the Attorney General. Citizens of countries of concern located in the United States are treated as U.S. persons, rather than covered persons.
II. Key Elements of Data Transactions Covered by the Rules
A. Types of Data
The restrictions on transactions apply in separate ways to two types of data: government-related data, and bulk U.S. sensitive personal data. Government-related data refers to any precise geolocation data, regardless of volume, for any location within certain sensitive areas, and also includes sensitive personal data, regardless of volume, that is linkable to certain current or former U.S. government employees, contractors, or officials. Meanwhile, bulk U.S. sensitive personal data is data that is linked or linkable to any identifiable U.S. individual, or to a discrete and identifiable group of U.S. persons, regardless of whether the data is anonymized, pseudonymized, de-identified, or encrypted, and includes: 1) covered personal identifiers, 2) precise geolocation data, 3) biometric identifiers, 4) human genomic data, 5) personal health data, and 6) personal financial data. For a set of data to be considered “bulk,” it must cover a specified number of U.S. persons on a sliding scale specific to each type of data (e.g., genomic information on more than 100 persons is considered bulk human genomic data).
Of particular interest for life sciences companies are the following categories of bulk U.S. sensitive personal data: human genomic data and personal health data. Human genomic data is defined as the nucleic acid sequences that constitute genetic instructions found in a human cell, such as the results of an individual’s genetic test. Under the proposed rules, the restrictions on human genomic data also apply to any human biospecimen—such as tissue, blood, or urine—from which such genomic data can be derived. Other ‘omic data (e.g., epigenomic, glycomic, lipidomic, metabolomic, meta-multiomic, microbiomic, phenomic, proteomic, and transcriptomic data) is not currently part of the proposed regulation, although the NPRM states that the DOJ is considering regulating such other ‘omic data in the final rule and welcomes public comments on the health, economic, or scientific impact if such regulation is enacted.
Meanwhile, personal health data includes physical or mental health data such as physical measurements, diagnostics, interventions, test results, immunization data, and prescribed medications. Importantly, because aggregated and anonymized data is not exempt, and because many clinical datasets contain data within this broad definition of “personal health data,” sharing of clinical data with covered persons may constitute “data brokerage” (as discussed below) and thus be barred with respect to covered persons unless it is otherwise not covered (e.g., the “bulk” thresholds are not met) or it is subject to specific exemptions (as discussed below).
B. Types of Transactions
Covered data transactions are transactions that involve any access to any government-related data or bulk U.S. sensitive personal data and that involve one of the following types of agreements: 1) data brokerage, 2) vendor agreement, 3) employment agreement, or 4) investment agreement.
The definition of “access” in the NPRM remains extremely broad, covering, inter alia, “logical or physical access, including the ability to obtain, read, copy, decrypt, edit, divert, release, affect, alter the state of, or otherwise view or receive” data “in any form.” This extremely broad language has been brought over by the DOJ from the Committee on Foreign Investment in the United States (CFIUS) context, where the breadth of this form of “access” has caused significant problems for companies striving to comply with their CFIUS mitigation agreements that limit access to data. For example, nearly any employment agreement with a covered person would be subject to relevant restrictions if that individual would gain access to the employer’s intranet, assuming bulk personal data could be viewed on that network. The difficulty of determining the many possible types of “access” to data that general network logins grant may cause larger companies to consider any agreement of the covered types with a covered person to be subject to these rules.
The strongest controls in the NPRM apply to data brokerage transactions. A data brokerage transaction under the proposed rules is a commercial transaction (e.g., a sale or license) that transfers data to a recipient that did not collect or process the data directly from the individuals linked to the collected or processed data. The other three categories are similarly broadly defined. Employment agreements include any agreement in which an individual performs work for a person in exchange for consideration, including board or advisory committee work if compensated. Investment agreements include any agreement in which a person exchanges consideration for direct or indirect ownership interests in or rights in relation to a U.S. legal entity or U.S. real estate. Vendor agreements include any agreements other than employment agreements in which any person provides goods or services to another person in exchange for consideration. Many kinds of commercial agreements will ultimately fall into one of these four categories.
C. Exemptions
Exempt transactions include those for the conduct of the official business of the United States Government, transactions conducted pursuant to an agreement (e.g., grant, contract) entered into with the United States Government,4 corporate group transactions between a U.S. person and its subsidiary or affiliate in a country of concern that is ordinarily incident to business operations,5 and investment agreements subject of a CFIUS action.6Importantly for life sciences companies, certain transactions related to activities involving the U.S. Food and Drug Administration (FDA) are exempt, such as those ordinarily incident to and part of clinical investigations regulated by the FDA, and those that support applications to the FDA for research or marketing permits for drugs. Relatedly, transactions involving regulatory approval data that is de-identified and required to be submitted to a regulatory entity in a country of concern to obtain or maintain authorization or approval for drugs, biological products, or medical devices is exempt.7
However, in the form currently proposed in the NPRM, these exemptions have clear limitations. For example, the exemption for sharing data to obtain regulatory approval for drugs in a country of concern is limited to data that is: i) de-identified; ii) required by a regulatory entity to obtain or maintain authorization or approval to research or market a drug, biological product, device, or combination product (collectively “covered product”); and iii) reasonably necessary to evaluate the safety and effectiveness of the covered product. In addition, use of this exemption requires compliance with certain recordkeeping rules otherwise applicable to restricted transactions.
The DOJ has also invited comment on the scope of the exemptions from the public, including in particular the exemption for activities that are ordinarily incident to and part of clinical investigations regulated by the FDA. For example, the DOJ has indicated that it does not currently intend to categorically preclude clinical investigations from being conducted in a country of concern, but that it will accept comments on that point.
III. Prohibited and Restricted Transactions and Affirmative Reporting Obligations
U.S. persons are prohibited from knowingly8 engaging in three specific types of covered data transactions9 unless those transactions are otherwise authorized under an exemption or a license from DOJ:
- data brokerage transactions with a covered person involving any type of bulk sensitive personal data or government-related data on U.S. persons;
- data brokerage transactions with any foreign person involving any type of bulk sensitive personal data or government-related data on U.S. persons unless contractual clauses are included stopping that foreign person from engaging in further data brokerage with covered persons; and
- agreements with a covered person involving data brokerage or vendor, employment, and non-passive investment agreements with a covered person if such agreements involve access to bulk U.S. person human genomic data (again, including biospecimens from which such data can be derived).
As noted in the second bullet, U.S. persons must include contractual language requiring foreign counterparties to any data brokerage agreement (e.g., any data license) to restrict retransfer of the data in question. U.S. persons engaged in such data brokerage with a foreign person should take reasonable steps to evaluate whether the foreign person is complying with the contractual provision, as a failure to conduct adequate due diligence could subject the U.S. person to enforcement action.
Moreover, even though the rule only restricts the actions of U.S. persons, many non-U.S. persons may still be impacted by the final rule. More specifically, the proposed rules restrict U.S. persons from “knowingly directing” activity at foreign entities that would be a prohibited transaction for a U.S. person. U.S. citizens in a position to affect decision-making at a foreign business not otherwise bound by the rule, such as officers and directors of that entity, are obliged not to use their authority to direct the foreign entity to enter into agreements that are prohibited or restricted without complying with the rules. As a result, many foreign entities may end up subject to the Meanwhile, U.S. persons are restricted from knowingly engaging in covered data transactions that are vendor,10 employment,11 and non-passive investment agreements12 involving access to any of the other non-human-genomic-data types of sensitive data. Restricted transactions are only allowed if certain security procedures are implemented with respect to the protection of the data, a third party is employed to audit security, and recordkeeping and DOJ reporting obligations are followed.13 The security requirements are not yet finalized, and the CISA has provided an opportunity for comments from the public on the proposed requirements.14
Beyond the sets of prohibited and restricted transactions, there is also an affirmative reporting obligation for “any U.S. person that has received and affirmatively rejected (including automatically rejected using software, technology, or automated tools) an offer from another person to engage in a prohibited transaction involving data brokerage,” even if no such transaction was ever entered into.
IV. Penalties
Noncompliance with the proposed rules may result in a civil or criminal penalty. Consistent with the underlying presidential statutory authorities under which the original executive order was issued, the maximum civil monetary penalty for a violation is the greater of $368,136 or an amount that is twice the amount of the transaction that is the basis of the violation. Criminal penalties may include fines of not more than $1,000,000, or if a natural person, imprisonment for not more than 20 years, or both.
V. Considerations for Technology Companies
Implementation of the Executive Order is one of several steps the U.S. government has taken recently to address national security concerns by regulating transactions with certain countries and persons deemed to pose an unacceptable risk to the United States. This includes issuance by the U.S. Treasury Department of final rules implementing Executive Order 14105 on outbound U.S. investment with a target entity having ties to China.15 However, the change in administration may alter the current course of national security measures, and the proposed rule set forth in the NPRM is not the final rule.
Technology companies that may be affected by the proposed rule may submit comments by November 29, 2024.16
For more information, please contact any member of the national security, data, privacy, and cybersecurity, and patents and innovations practices at Wilson Sonsini Goodrich & Rosati.
Appendix: Select Example Transactions
Example Prohibited Transactions
Example § 202.305(b)(3): A U.S. person is employed at a U.S.-headquartered multinational company that has a foreign affiliate that is not a covered person. The U.S. person instructs the U.S. company's compliance unit to change (or approve changes to) the operating policies and procedures of the foreign affiliate with the specific purpose of allowing the foreign affiliate to undertake covered data transactions that would be prohibited if performed by a U.S. person. The U.S. person has knowingly directed prohibited transactions.
Example § 202.214(b)(4): A U.S. company owns and operates a mobile app for U.S. users with available advertising space. As part of selling the advertising space, the U.S. company provides the bulk precise geolocation data, IP address, and advertising IDs of its U.S. users' devices to an advertising exchange based in a country of concern. The U.S. company's provision of this data as part of the sale of advertising space is data brokerage and a prohibited transaction.
Example § 202.217(b)(3): A U.S. company has derived U.S. persons' biometric identifiers by scraping public photos from social media platforms. The U.S. company stores the derived biometric identifiers in bulk, including face-data scans, for the purpose of training or enhancing facial-recognition software. The U.S. company intends to hire a foreign person, who primarily resides in a country of concern, as a project manager responsible for the database. The agreement retaining the project manager would be an employment agreement. The individual's employment as the lead project manager would involve access to the bulk biometric identifiers. The project manager's employment would be a restricted transaction.
Example Restricted Transactions
Example § 202.217(b)(1): A U.S. company that conducts consumer human genomic testing collects and maintains bulk human genomic data from U.S. consumers. The U.S. company has global IT operations, including employing a team of individuals who are citizens of and primarily resident in a country of concern to provide back-end services. The agreements related to employing these individuals are employment agreements. Employment as part of the global IT operations team includes access to the U.S. company's systems containing the bulk human genomic data. These employment agreements would be prohibited transactions (because they involve access to bulk human genomic data).
Example § 202.258(b)(3): A U.S. company, which is owned by an entity headquartered in a country of concern and has been designated a covered person, establishes a new data center in the United States to offer managed services. The U.S. company's data center serves as a vendor to various U.S. companies to store bulk U.S. sensitive personal data collected by those companies. These vendor agreements are restricted transactions.
Example § 202.228(c)(1): A U.S. company intends to build a data center located in a U.S. territory. The data center will store bulk personal health data on U.S. persons. A foreign private equity fund located in a country of concern agrees to provide capital for the construction of the data center in exchange for acquiring a majority ownership stake in the data center. The agreement that gives the private equity fund a stake in the data center is an investment agreement. The investment agreement is a restricted transaction.
Example § 202.258(b)(1): A U.S. company collects bulk precise geolocation data from U.S. users through an app. The U.S. company enters into an agreement with a company headquartered in a country of concern to process and store this data. This vendor agreement is a restricted transaction.
Example Exemptions
Example § 202.510(d)(1): A U.S. pharmaceutical company seeks to market a new drug in a country of concern. The company submits a marketing application to the regulatory entity in the country of concern with authority to approve the drug in the country of concern. The marketing application includes the safety and effectiveness data reasonably necessary to obtain regulatory approval in that country. The transfer of data to the country of concern's regulatory entity is exempt from the prohibitions in this part.
Example § 202.510(d)(2): Same as Example 1, except the regulatory entity in the country of concern requires that the data be de-anonymized. The transfer of data is not exempt under this section, because the data includes sensitive personal data that is identified to an individual.
Example § 202.510(d)(3): Same as Example 1, except the U.S. company enters a vendor agreement with a covered person located in the country of concern to store, organize, and prepare the bulk U.S. sensitive personal data for submission to the regulatory agency. The transaction is not exempt under this section, because the use of a covered person to prepare the regulatory submission is not necessary to obtain regulatory approval.
Example § 202.504(b): A U.S. hospital receives a federal grant to conduct human genomic research on U.S. persons. As part of that federally funded human genomic research, the U.S. hospital contracts with a foreign laboratory that is a covered person, hires a researcher that is a covered person, and gives the laboratory and researcher access to the human biospecimens and human genomic data in bulk. The contract with the foreign laboratory and the employment of the researcher are exempt transactions but would be prohibited transactions if they were not part of the federally funded research.
Example § 202.508(b)(3): A U.S. biotechnology company is acquired by a foreign multinational corporation. CFIUS reviews this acquisition and concludes action without mitigation. This acquisition is not subject to a CFIUS action, and the acquisition remains subject to this part to the extent otherwise applicable.
Example § 202.509(b)(2): A U.S. telecommunications service provider collects precise geolocation data on its U.S. subscribers. The U.S. telecommunications service provider sells this precise geolocation data in bulk to a covered person for the purpose of targeted advertising. This sale is not ordinarily incident to and part of the provision of telecommunications services and remains a prohibited transaction.
[1] https://www.regulations.gov/document/DOJ-NSD-2024-0004-0001; 28 CFR Part 202.
[2] https://www.federalregister.gov/documents/2024/03/01/2024-04573/preventing-access-to-americans-bulk-sensitive-personal-data-and-united-states-government-related.
[3] See Examples at § 202.211(b)(1)-(b)(5).
[5] See Example § 202.506(b)(4).
[6] See Example § 202.508(b)(3)-(b)(7).
[7] See Examples § 202.510(d)(1)-(d)(3).
[8] See Examples at § 202.230(b)(1)-(b)(8).
[9] See Examples at § 202.210(b), § 202.214(b)(1)-(b)(6).
[10] See Examples at § 202.258(b)(1)-(b)(4).
[11] See Example at § 202.217(b)(1).
[12] See Example at § 202.228(c)(1).
[13] See Examples at § 202.401(c)(1)-(c)(2).
[14] https://www.regulations.gov/document/CISA-2024-0029-0001.
[15] https://www.wsgr.com/en/insights/the-new-national-security-rules-for-investing-us-capital.html.
[16] https://www.regulations.gov/commenton/DOJ-NSD-2024-0004-0001.
- Privacy Policy
- Terms of Use
- Accessibility










